Hello everyone after a long break, I hope you are all doing well. 🙂 Today, I will talk about how you can use Google, which you use almost every day, more efficiently. I hope it catches your interest!
This blog explains the use of Google Dork techniques for educational purposes. The information provided in this article should only be used for security research and ethical purposes. The focus is on passive reconnaissance and discovering publicly available information on the internet using Google.
Google Dork should not be used for illegal or harmful activities. In case of any misuse, the responsibility lies entirely with the user.
What is Google Dork and How Does It Work?
Google Dorking, also known as Google Hacking, but in this blog, I will refer to it as “Google Dork,” is a search technique developed to find information that is not easily found in regular queries by using advanced search operators offered by the Google search engine.
Google Dork is used by security researchers and cybersecurity experts to detect internet vulnerabilities and potential security risks. However, just as there are good uses for it, there are also bad uses. By using these types of search methods, it may be possible to access website vulnerabilities, site flaws, or private data that is not meant to be public.
I can almost feel your excitement, but before diving into how it’s done, let’s take a quick look at its history! 😁
History of Google Dork
The concept of Google Dork emerged in August 2002 when Chris Sullo included a plugin called Nikto security scanner version 1.20 with the ’nikto_google.plugin’ plugin; you can access Nikto version 1.20 here: Nikto 1.20. In December of the same year, Johnny Long began using Google search queries to detect vulnerable systems and hidden information. These types of search queries eventually came to be known as ‘Google Dorks’.
Initially, Google Dork started as a list of simple search queries, but over time it expanded into a large database of search queries. In 2004, this database was organized and named the Google Hacking Database (GHDB). You can access Google Hacking queries from here: Google Hacking queries. Over time, GHDB became a comprehensive resource that helped malicious users discover vulnerable systems and sensitive information.
What started as techniques used only through Google gradually spread to other search engines. With advancing technology, automated attack tools began to perform searches more quickly and efficiently. These tools could easily find anything from vulnerable systems to databases using special queries.
However, Google Dorking has not always been used for malicious purposes. Sometimes, it can be used simply to quickly find a specific file or keyword. In fact, security experts may use this method to check whether companies unknowingly publish sensitive data on the internet. In this way, they can detect and report information leaks that could make companies vulnerable to cyberattacks.
In October 2013, anonymous attackers, according to security researchers, used Google Dorking to find websites running outdated versions of an instant messaging software. By searching for vulnerability indicators, the attackers gained control of 35,000 websites and created new administrator accounts.
In August 2011, anonymous actors used Google Dorking to discover a vulnerable File Transfer Protocol (FTP) server at a U.S. university, which led to the theft of personal information from approximately 43,000 faculty members, staff, students, and alumni, as reported by an information technology security firm.
Google Dork Timeline
If you want to explore the historical developments related to Google Dork, you can view the Google Dork Timeline here.
The Google Hacking Diggity Project is a research and development initiative aimed at quickly identifying security vulnerabilities in systems and accessing sensitive data within corporate networks using search engines like Google and Bing. This project seeks to develop the latest techniques and methods to detect security flaws by utilizing open-source information available on the internet. If you’re curious, you can find many resources by searching for the Diggity Project. However, I won’t go into further detail here. Now, if you’re ready, let’s get started.
Google Dork Commands
Since the documentation for Google’s dork commands can change over time, the following list does not cover all commands. This list includes some commands known to provide effective results.
Restrictive Search Commands
When using restrictive search commands, do not leave a space between the command and the parameter. Example usage is shown in the images below. Otherwise, Google may treat the command as a regular search term and it may not function as a dork.
site:
Allows you to search only within a specific website or domain. This command is especially useful when you want to search within a particular domain or website.
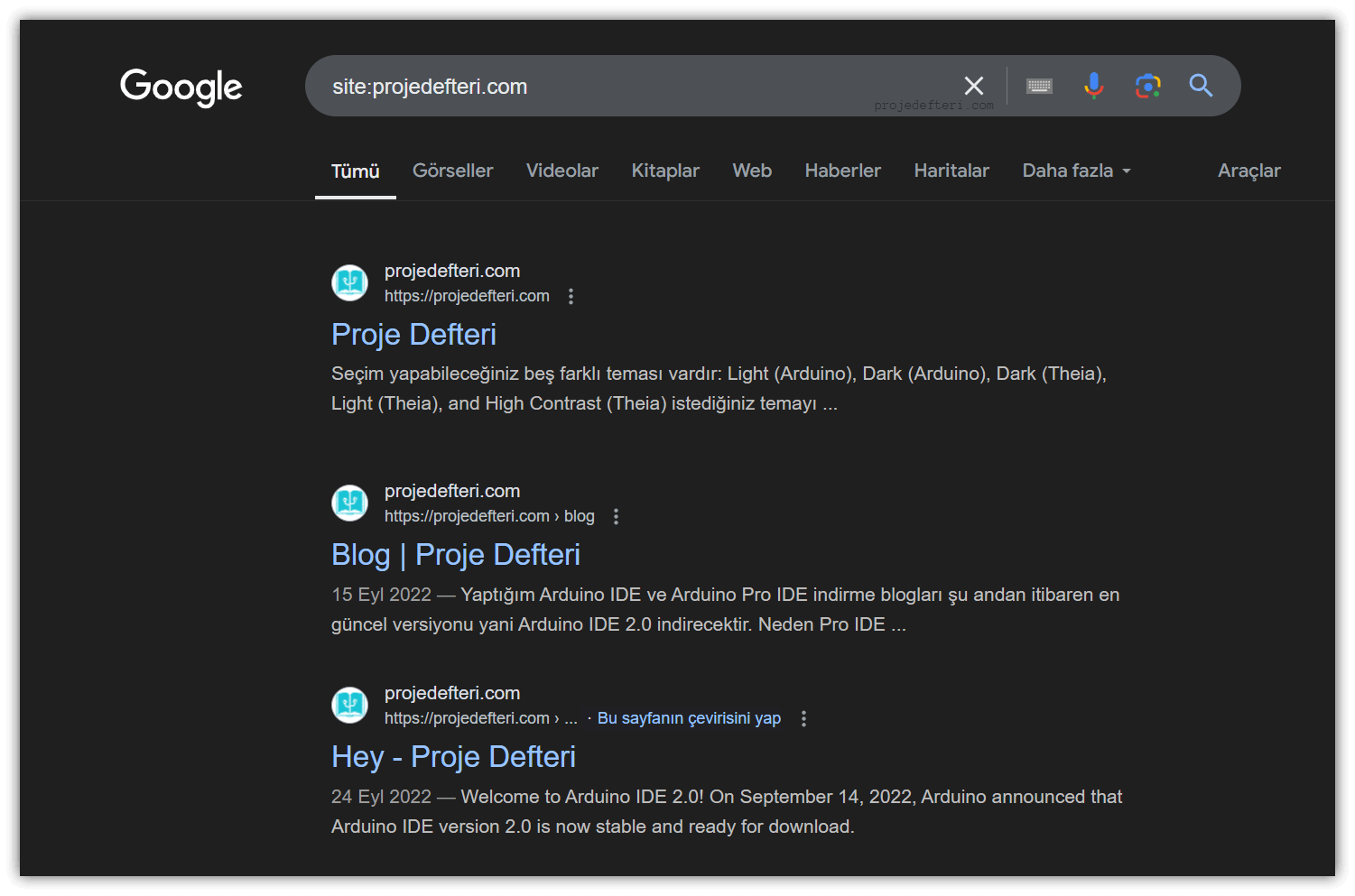
This command displayed results only from the projedefteri.com site.
filetype:
Searches for pages that contain a specific type of file. It is typically used to target file types like PDF, Excel, PowerPoint, etc.
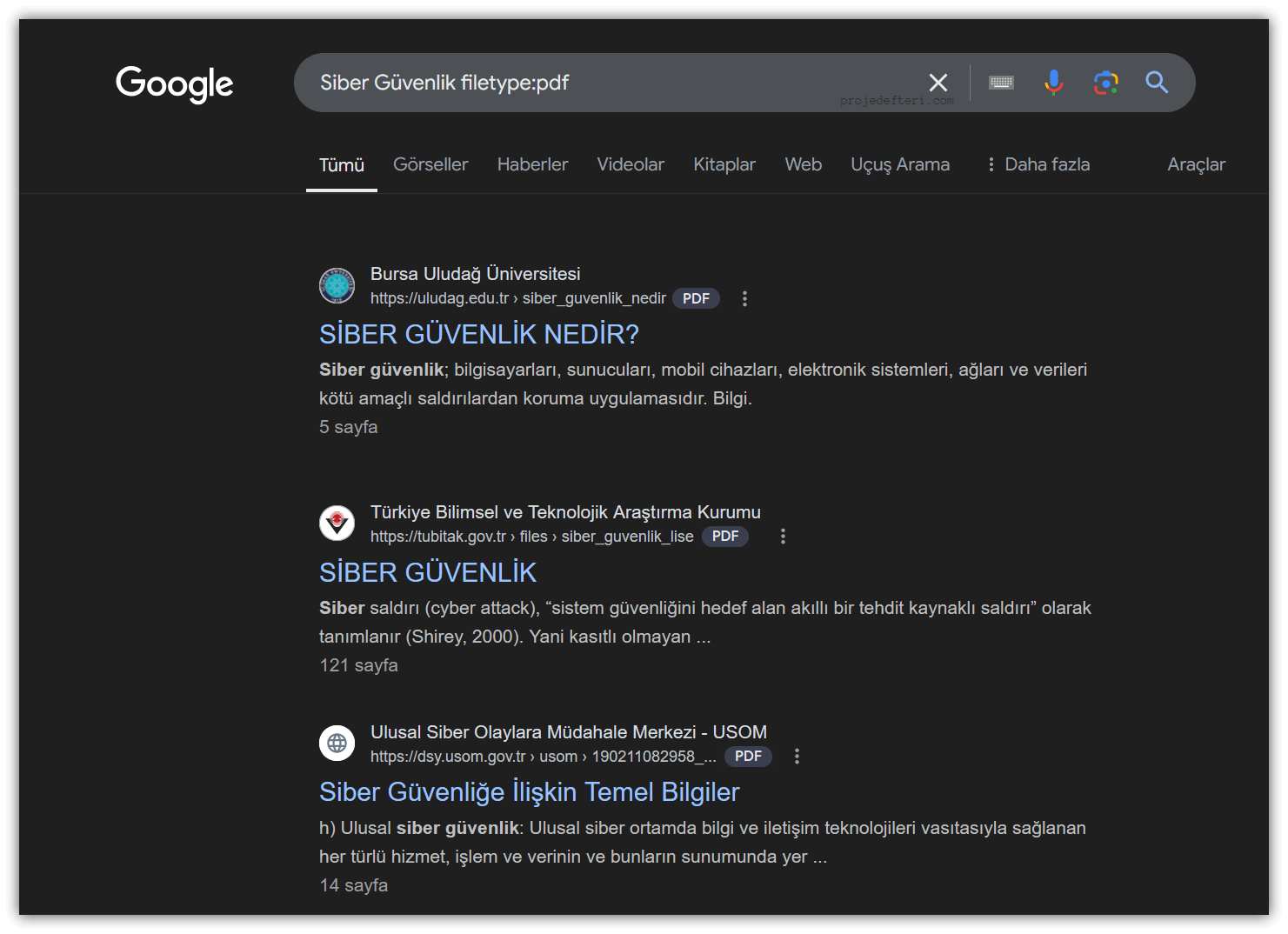
The filetype:pdf search command lists all PDF files related to Cyber Security.
define:
Used to quickly learn the meaning of a word or term.
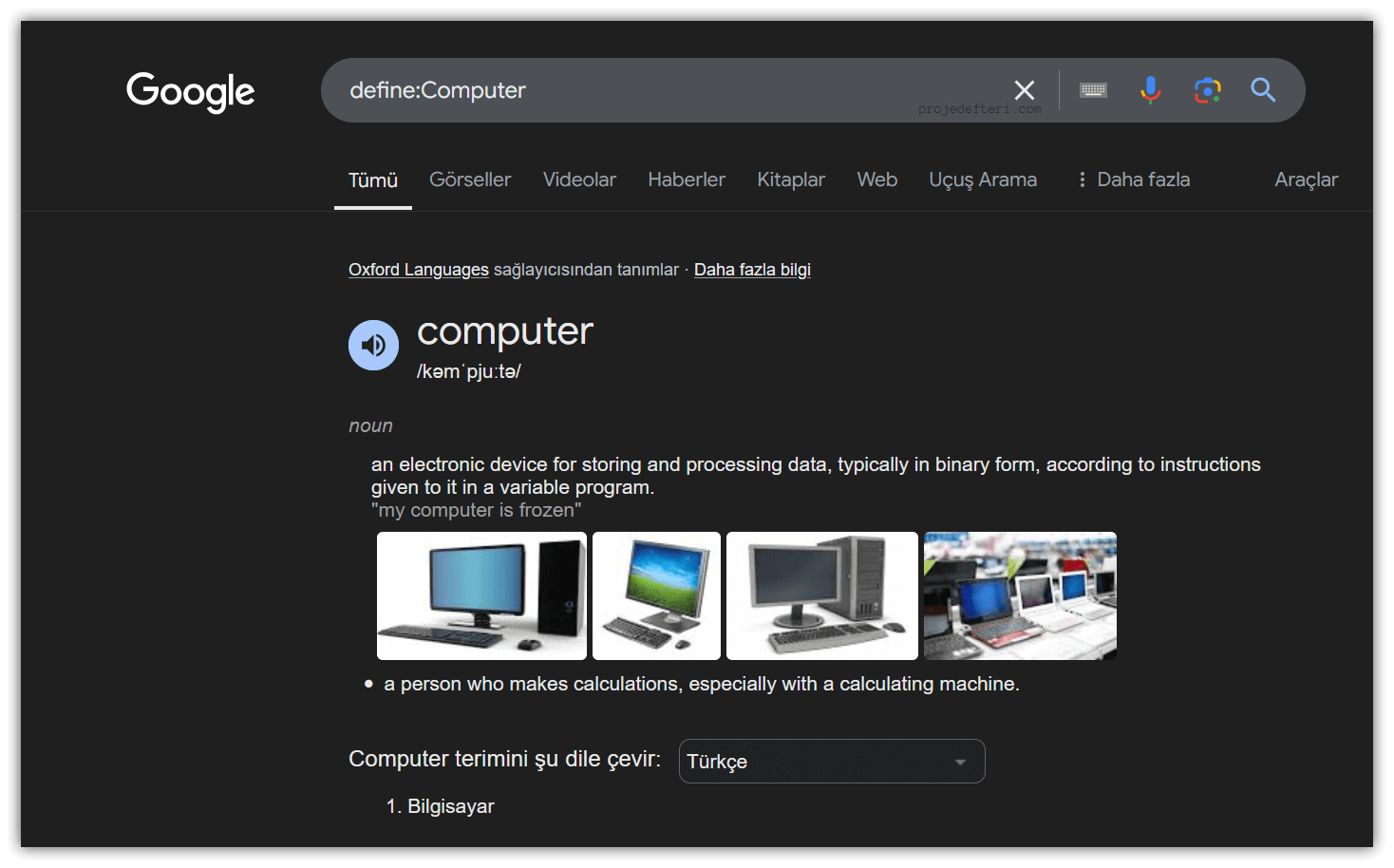
The define:Computer command allows you to search for the definition of the term “Computer.” This command often highlights various dictionary and encyclopedic definitions in the search results.
before:
Returns pages published before a specified date.
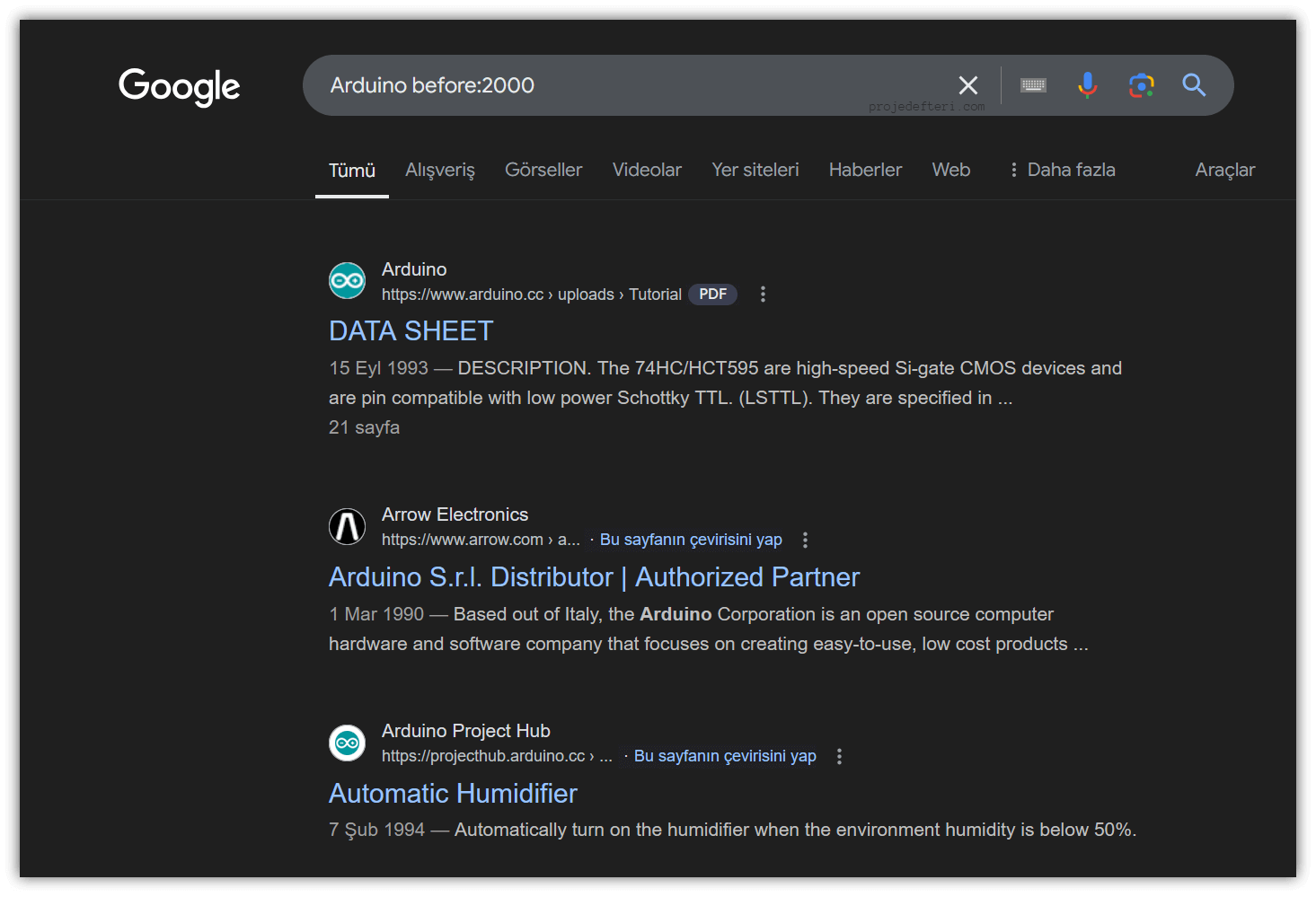
The before:2000 Arduino command lists content related to Arduino before the year 2000.
after:
Shows pages published after a specified date.
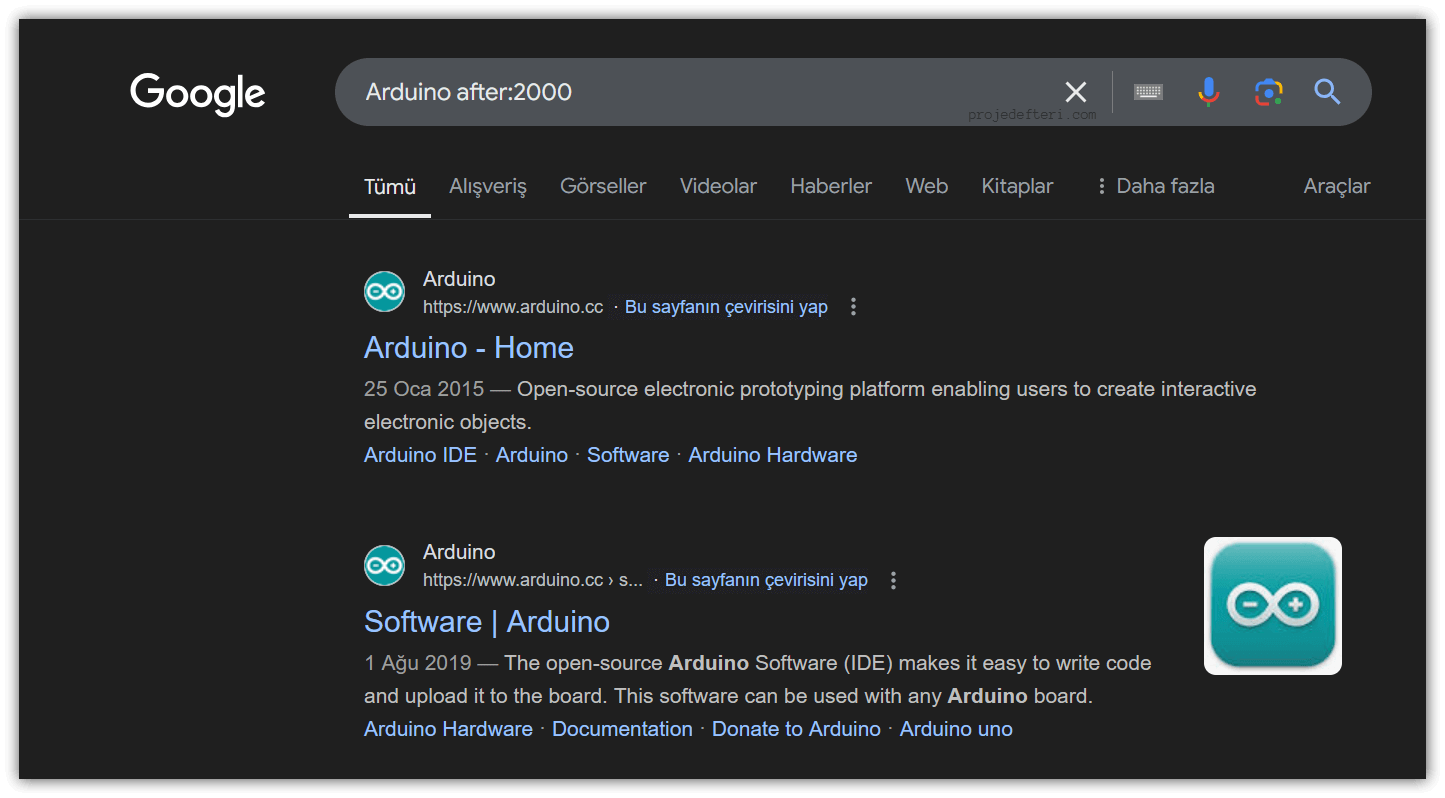
The after:2000 Arduino command lists content related to Arduino after the year 2000.
stocks:
A command that helps you quickly find stock and financial data.
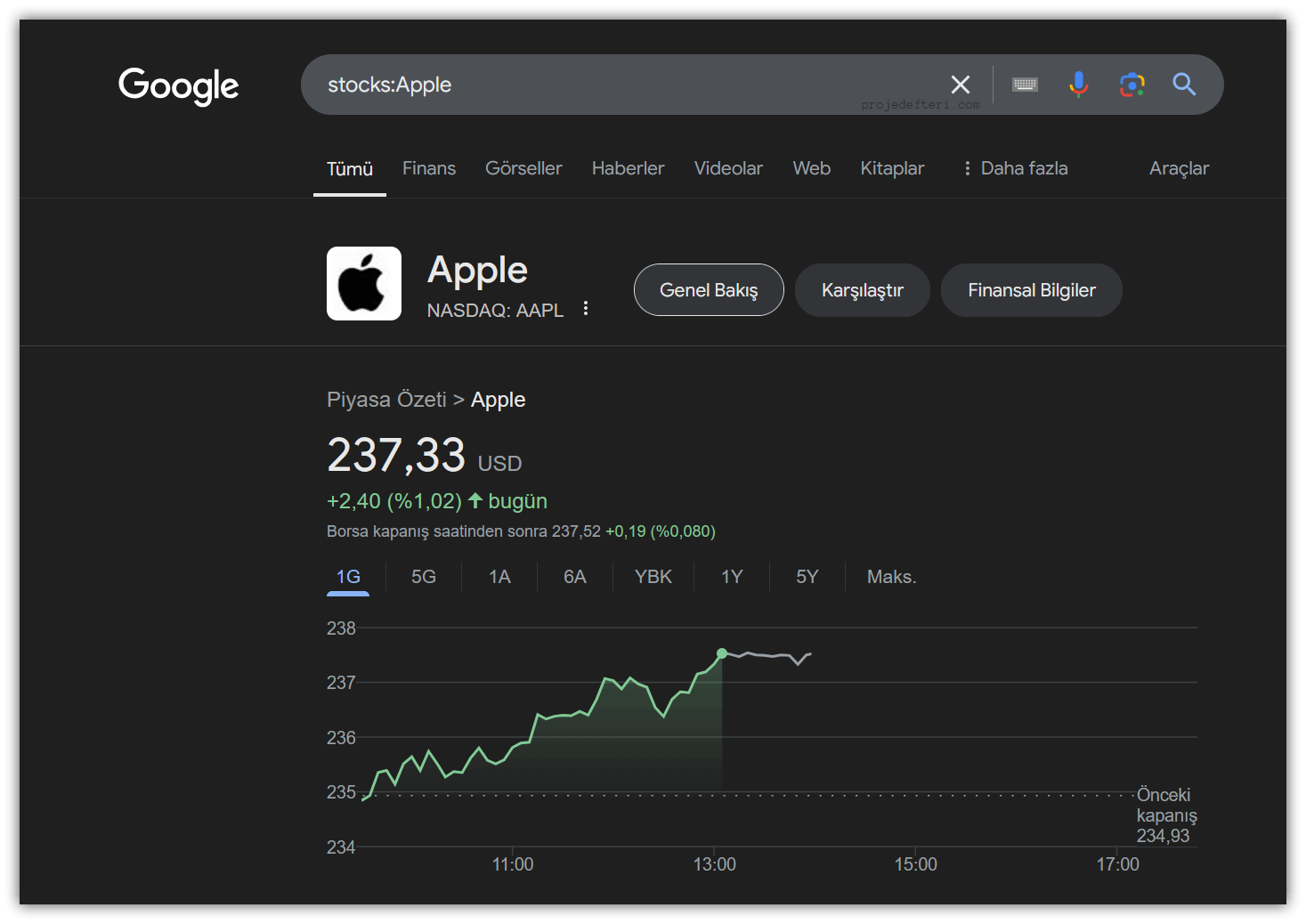
The stocks:Apple command searches for Apple Inc.’s stock price and market data on Google. This command helps you easily access Apple’s current stock market information.
movie:
Used to find information about a specific movie. This command can help you find articles, reviews, video content, and more related to films.
source:
Used to search for content from a specific source, often helpful for finding specific topics on news sites or media platforms.
Informative Search Commands
link:
This command searches for pages that link to a specific webpage. It is used to find other pages that link to a particular webpage.
cache:
Displays an older version of a page stored in Google’s cache. Google saves certain versions of pages, and this command is used to view those versions quickly.
related:
Shows websites that are similar to the specified website.
map:
Used to quickly search for a location’s map or map-related information.
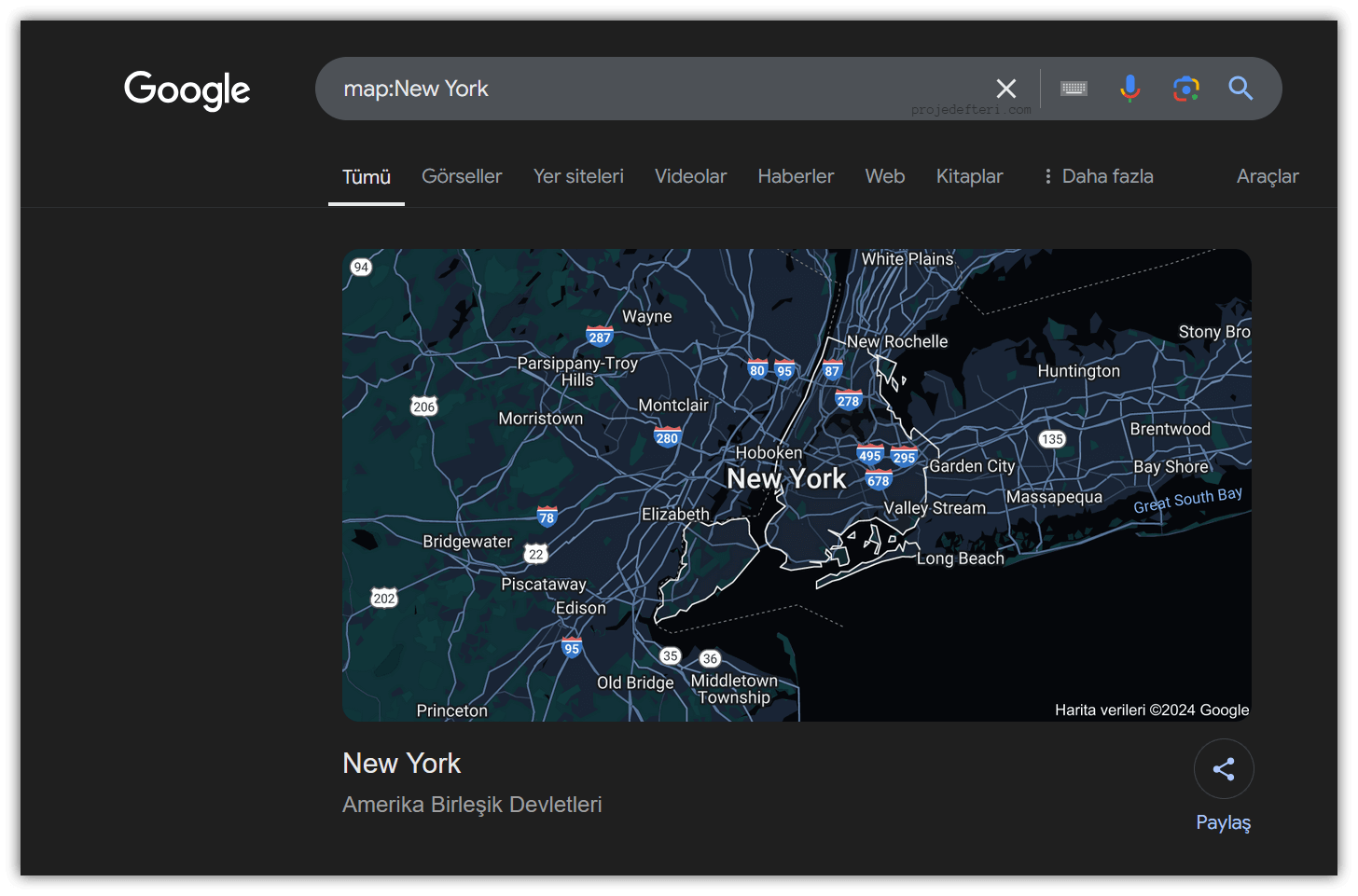
The map:New York command shows results displaying maps of New York City.
weather:
Used to quickly search for weather information for a specific area.
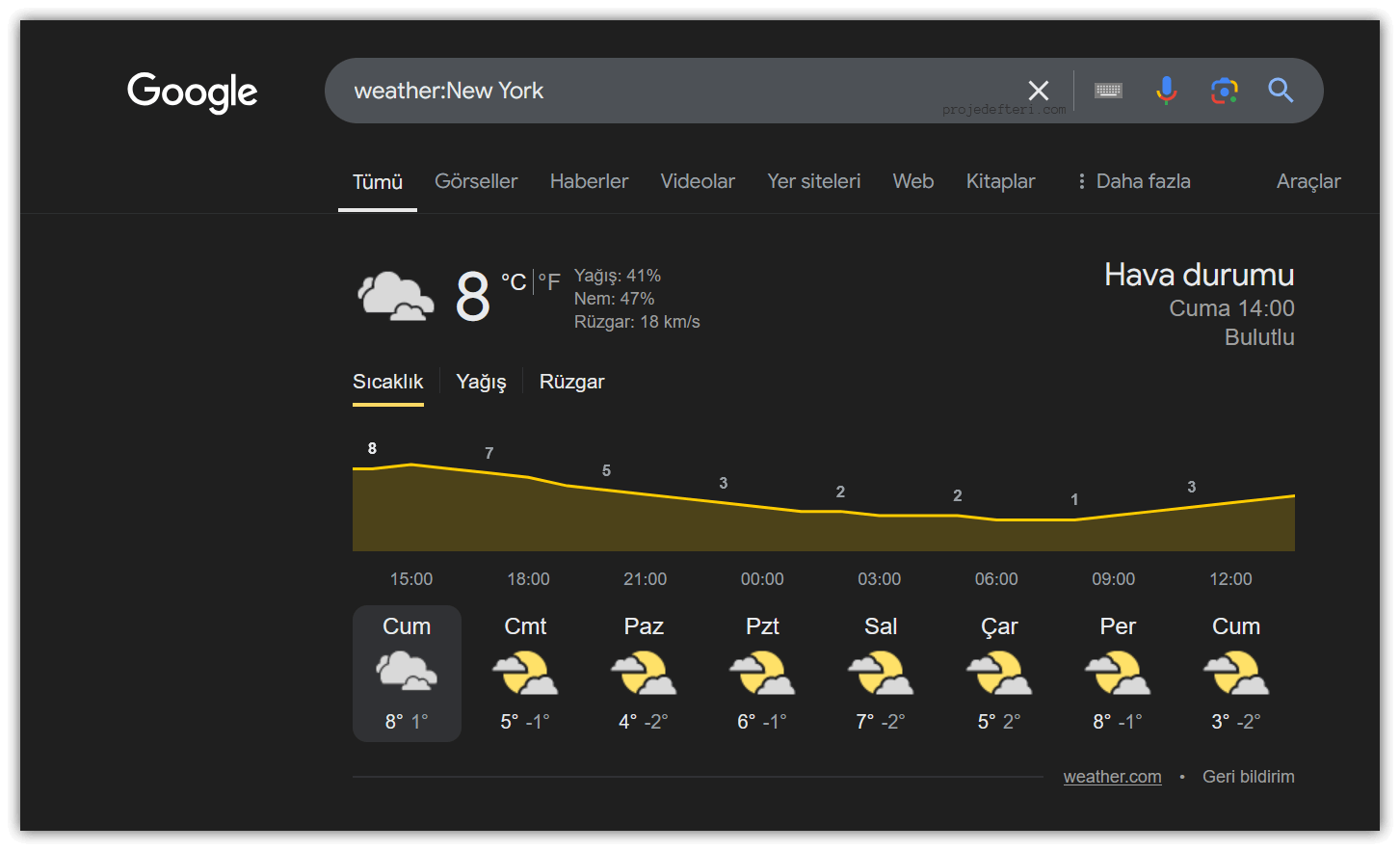
The weather:New York command displays weather information for New York.
Text Search Commands
inurl:
Allows you to search within a specific website or domain. Only content from the specified domain or site will be listed.
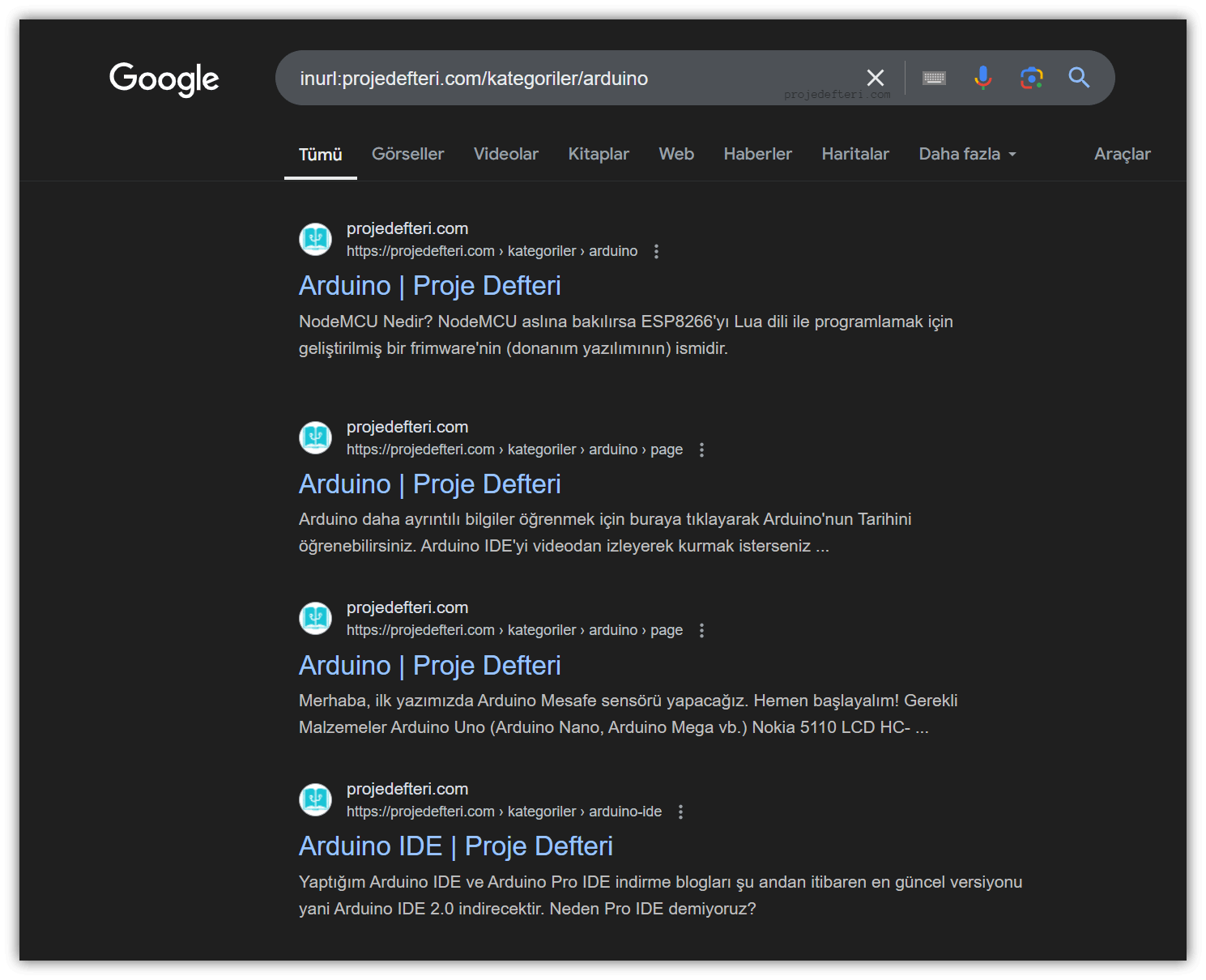
The inurl:projedefteri.com/kategoriler/arduino command searches for pages related to the “arduino” category on projedefteri.com. This command can help you find pages with a specific URL structure.
intext:
Searches for pages that contain a specific word within the page content.
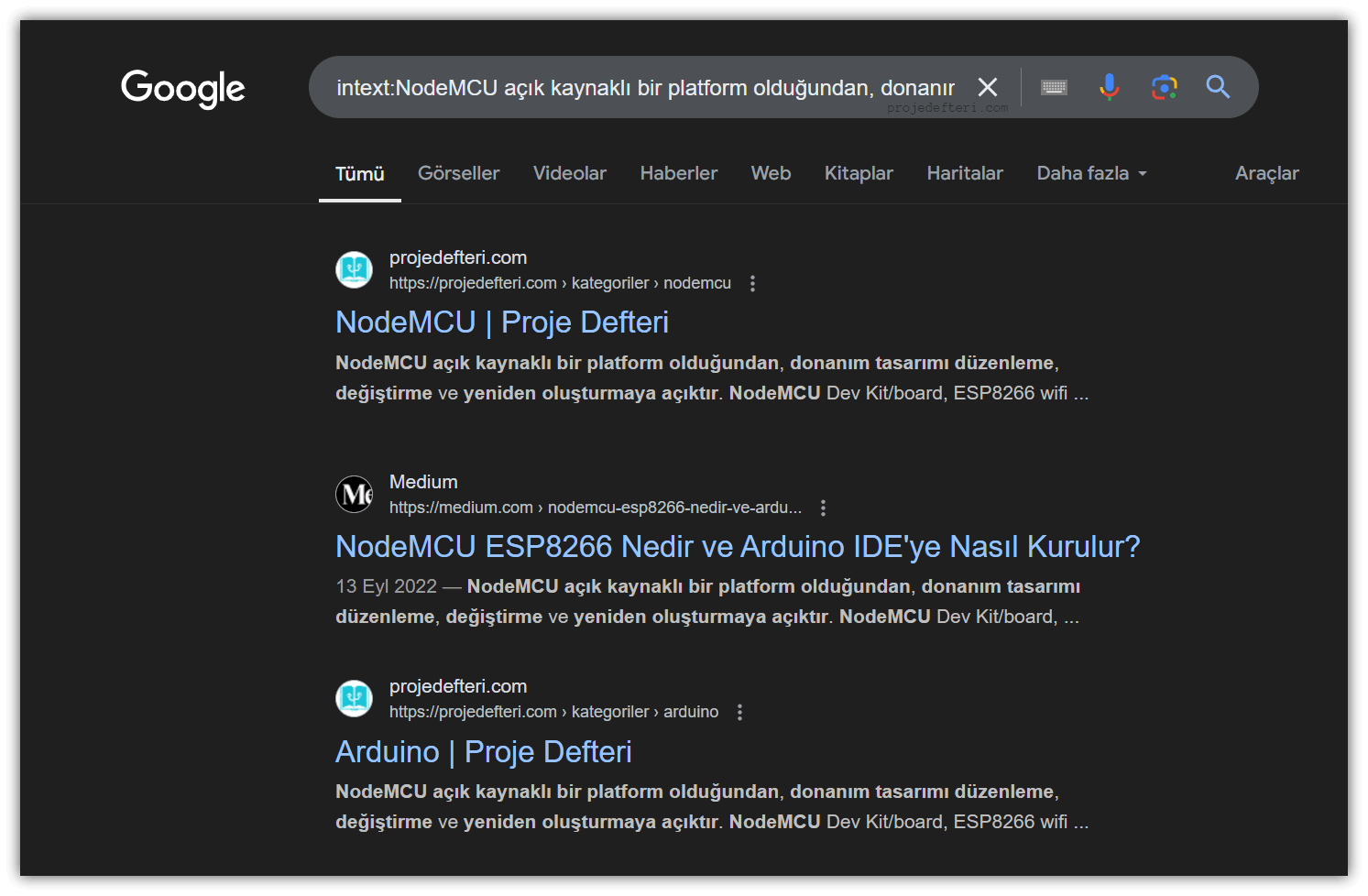
The intext:NodeMCU açık kaynak... command searches for pages containing the terms “NodeMCU” and “açık kaynak” in the content. Exact matches provide better results.
intitle:
Searches for a specific word or phrase in the page title.
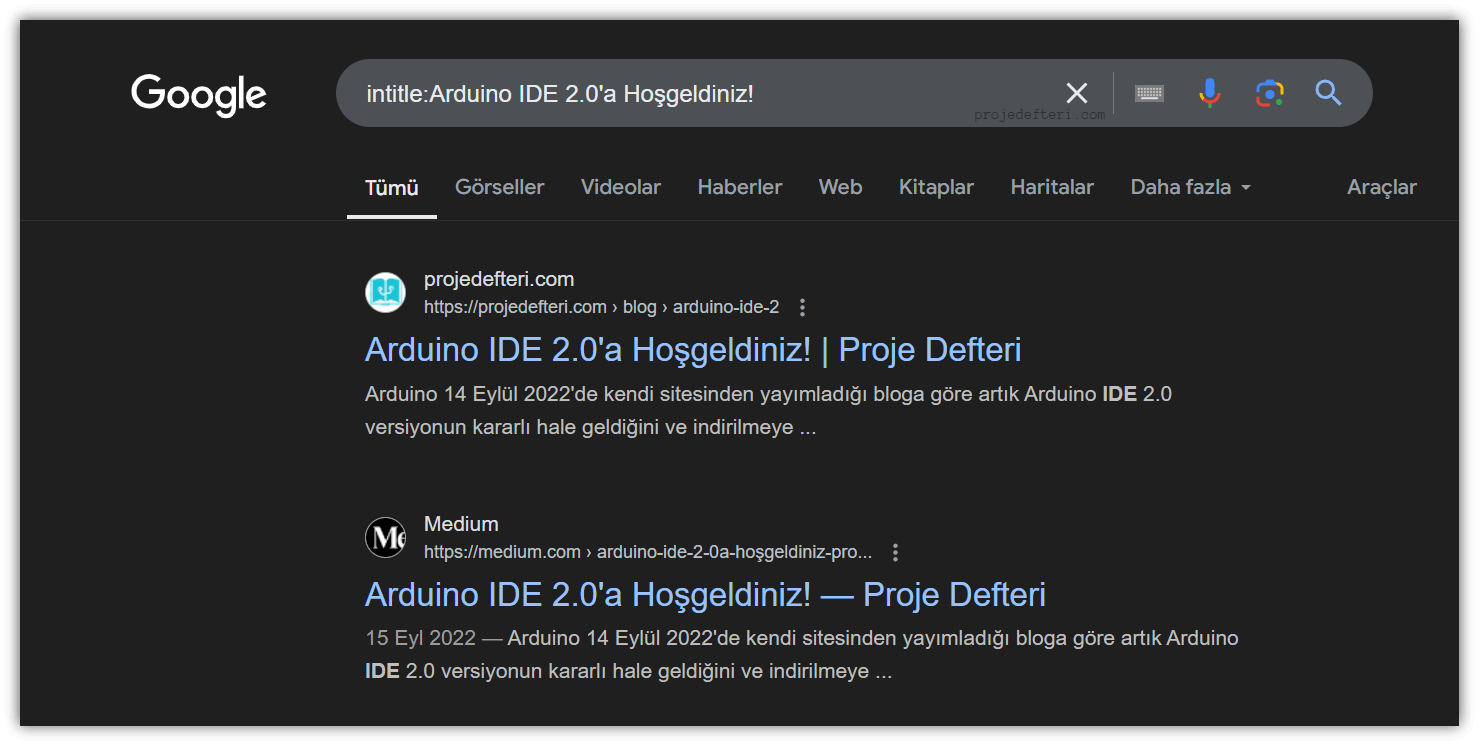
The intitle:Arduino IDE 2.0'a Hoşgeldiniz! command searches for pages with the title “Arduino IDE 2.0’a Hoşgeldiniz!”.
allinurl:
Searches for multiple words within the URL. The URL must contain all the specified words.
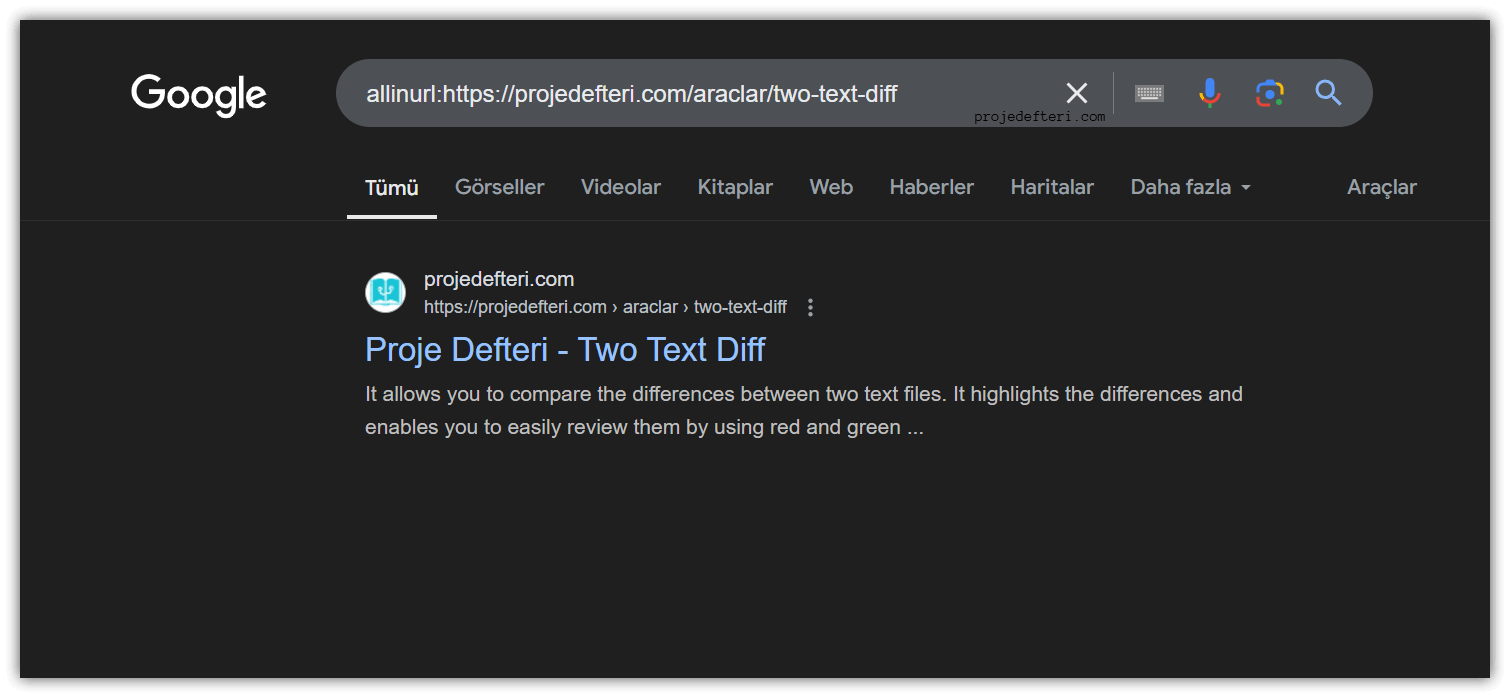
The allinurl:https://projedefteri.com/two-text-diff command searches for all pages on projedefteri.com with URLs containing the phrase “two-text-diff”.
allintitle:
Searches for multiple words in the page title. Lists pages that contain all the specified words in the title.
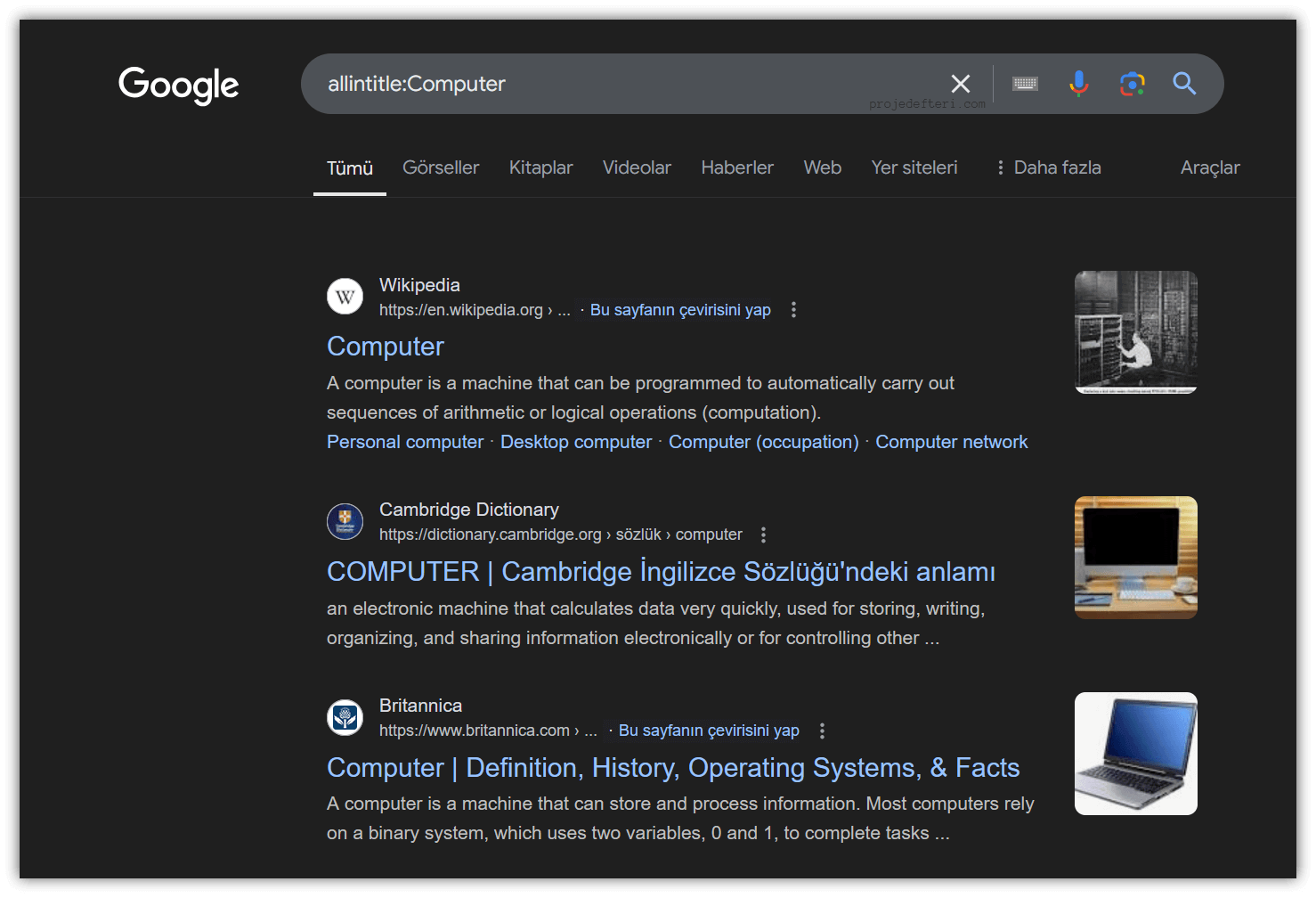
The allintitle:Computer command searches for all pages with “Computer” in the title.
allintext:
Searches for multiple words within the page content. All the specified words must be present in the page text.
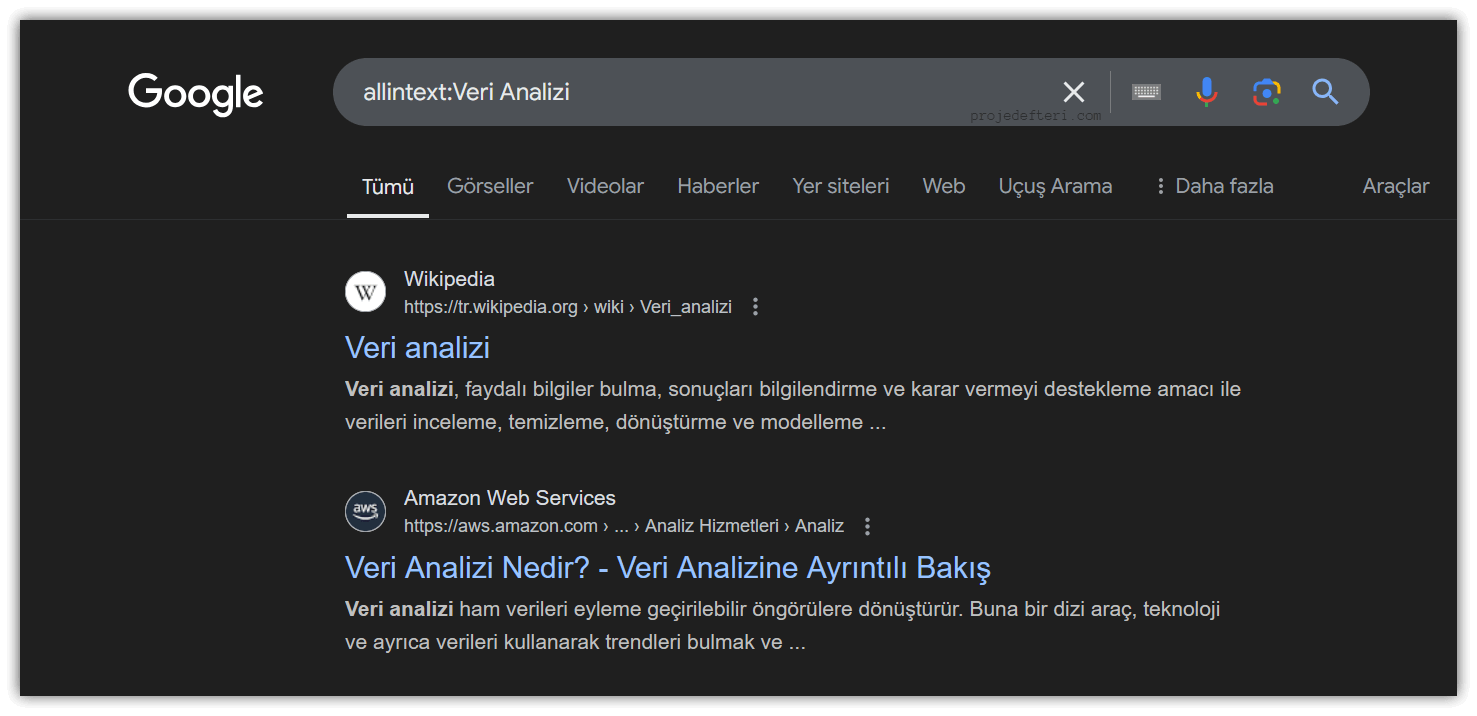
The allintext:Veri Analizi command searches for pages containing the phrase “Veri Analizi” in the content.
General Search Operators
Unlike some Google Dork commands, Google Dorking operators allow you to leave spaces between query elements. Additionally, you can use multiple operators and commands together to create more complex searches.
" "
When you search for a term inside quotation marks, the search engine looks for the exact term (with the word order and exact phrasing).
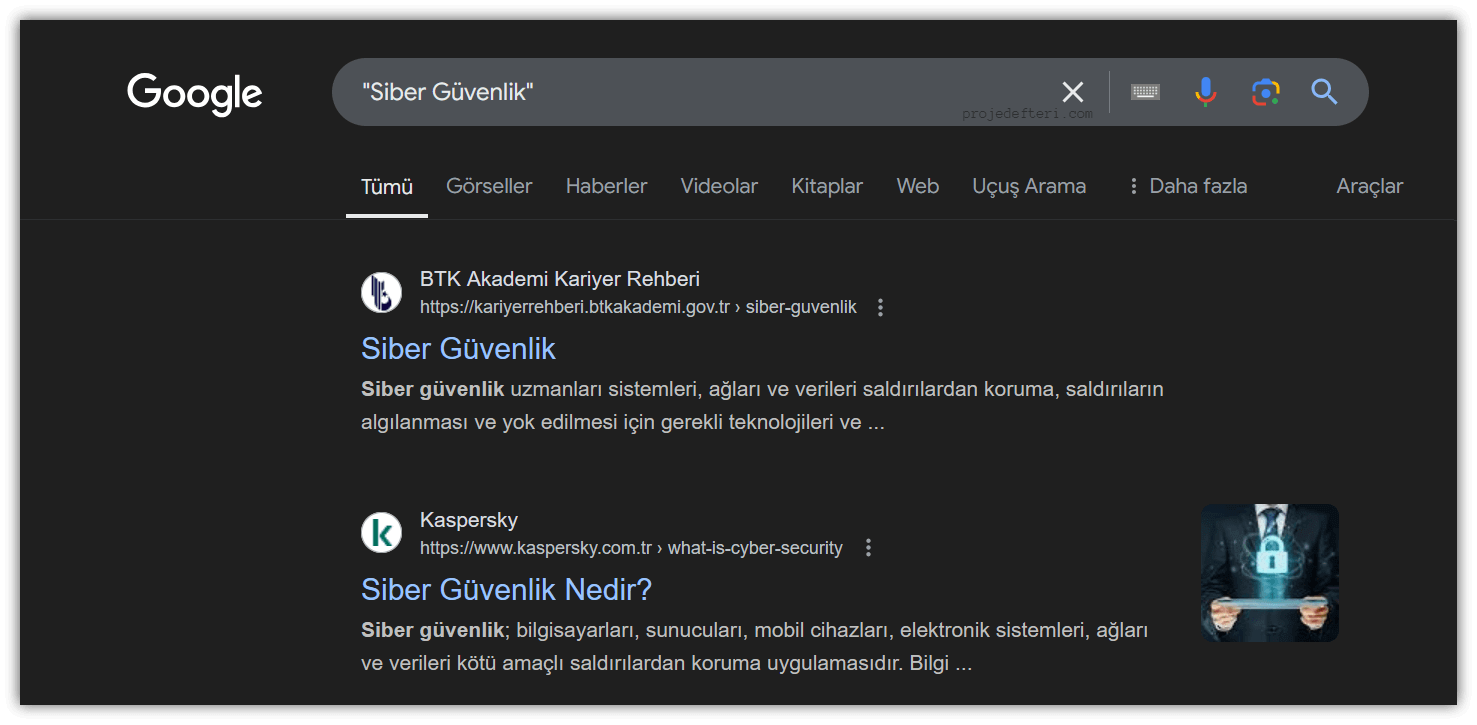
The "Siber Güvenlik" command searches for pages containing the exact phrase “Siber Güvenlik” in the title or content.
-
This operator excludes a specific term from the results. It is used to remove unwanted words or terms from the search query.
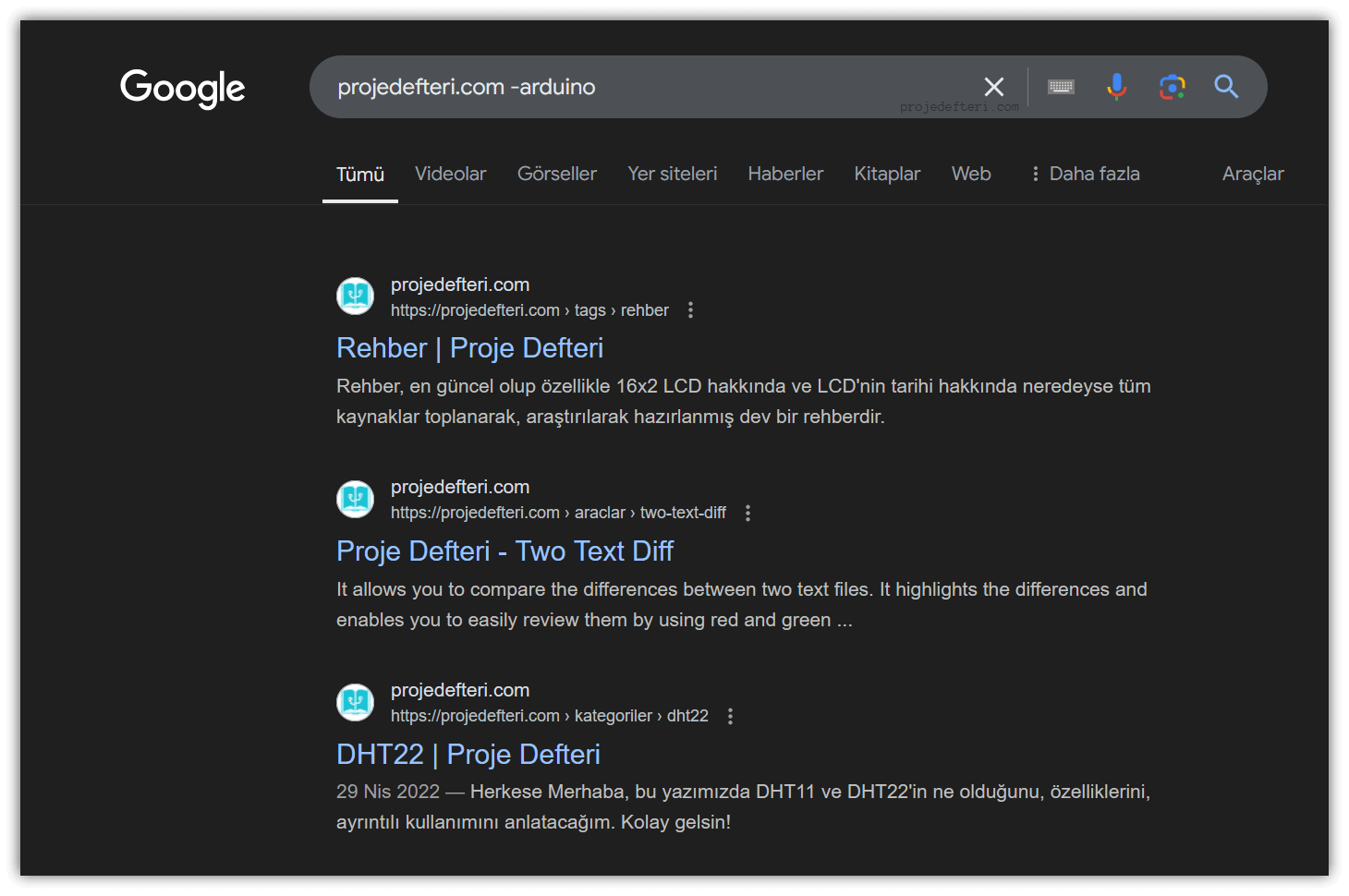
The projedefteri.com -arduino command searches for pages on projedefteri.com that do not contain the word “arduino,” effectively filtering out content related to Arduino.
*
Used as a wildcard to represent an unknown or variable word.
OR, |
This operator is used to find results that include one of two words or terms.
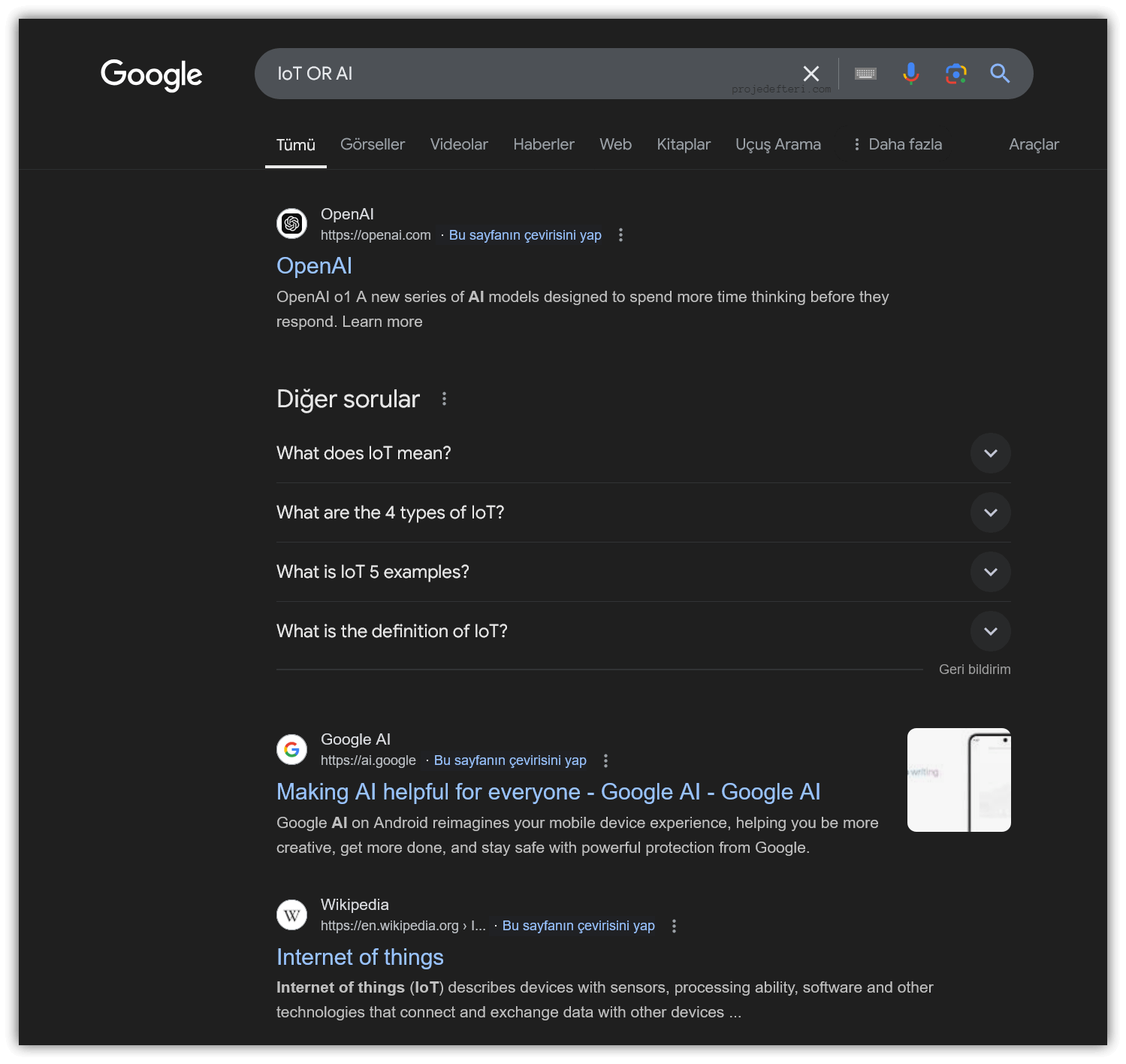
The IoT OR AI command searches for pages containing either IoT or AI. This command helps you find sources that include at least one of the two terms.
Conclusion 🙌🏻
This blog will help you reach what you’re searching for on Google faster and more efficiently. You can share your feedback in the comments section. Best of luck with your work and happy coding! 😊
